Project Introduction

In the world of cloud computing, infrastructure as code (IaC) plays a pivotal role in automating the deployment and management of resources. This blog post provides a step-by-step guide on creating a Two-Tier architecture on AWS using Terraform. We’ll explore the essential services involved, ensuring high availability, security, and scalability for hosting a static website.
Also, we are adopting a modular approach with enhanced security measures. The infrastructure is organized into dedicated modules, ensuring a scalable, maintainable, and secure deployment.
Directory Overview
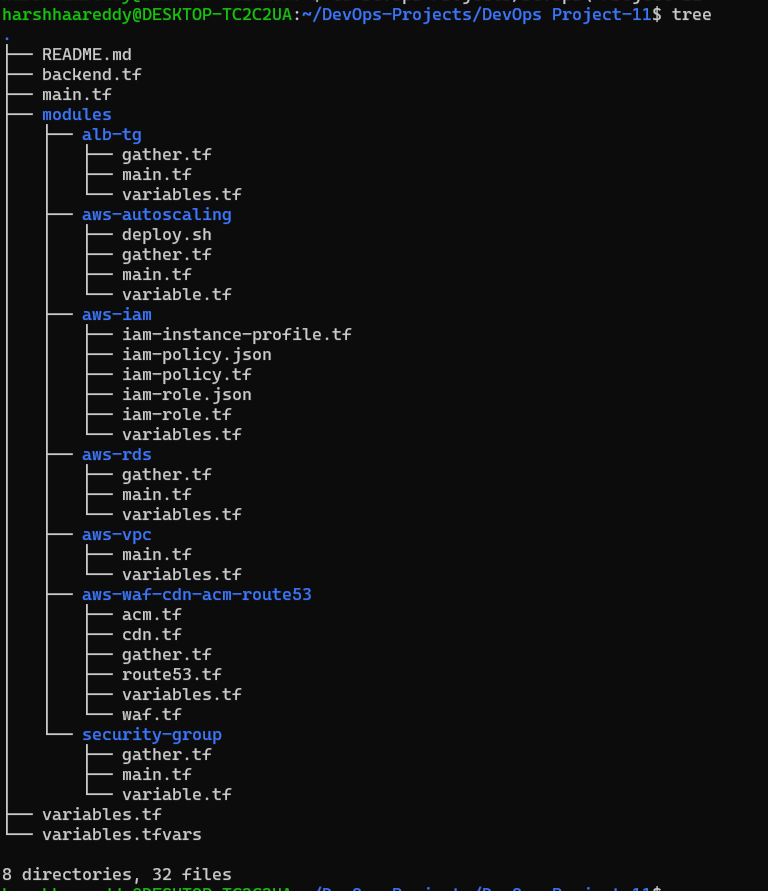
Directory Overview
- DevOps Project-11:
backend.tf: Configuration for Terraform backend, specifying where to store the Terraform state.main.tf: Main Terraform configuration orchestrating the deployment.variables.tf: Definition of variables used in the main Terraform configuration.variables.tfvars: Input values for the defined variables.- modules:
- alb-tg:
gather.tf: Terraform script to gather information about the Application Load Balancer (ALB) and Target Group (TG).main.tf: Main Terraform configuration for ALB and TG.variables.tf: Definition of variables used in the ALB and TG module.- aws-autoscaling:
deploy.sh: Shell script for deploying the Auto Scaling Group.gather.tf: Terraform script to gather information about the Auto Scaling Group.main.tf: Main Terraform configuration for the Auto Scaling Group.variable.tf: Definition of variables used in the Auto Scaling Group module.- aws-iam:
iam-instance-profile.tf: Terraform configuration for IAM instance profile.iam-policy.json: JSON file containing the IAM policy.iam-policy.tf: Terraform configuration for IAM policy.iam-role.json: JSON file containing the IAM role.iam-role.tf: Terraform configuration for IAM role.variables.tf: Definition of variables used in the IAM module.- aws-rds:
gather.tf: Terraform script to gather information about the RDS cluster.main.tf: Main Terraform configuration for the RDS cluster.variables.tf: Definition of variables used in the RDS module.- aws-vpc:
main.tf: Main Terraform configuration for the Virtual Private Cloud (VPC) and other Networking Services like Public/Private Subnet, ElasticIP, etc.variables.tf: Definition of variables used in the VPC module.- aws-waf-cdn-acm-route53:
acm.tf: Terraform configuration for ACM (Amazon Certificate Manager).cdn.tf: Terraform configuration for CDN (Content Delivery Network).gather.tf: Terraform script to gather information about WAF, CDN, ACM, and Route 53.route53.tf: Terraform configuration for Route 53.variables.tf: Definition of variables used in the WAF, CDN, ACM, and Route 53 modules.waf.tf: Terraform configuration for AWS WAF (Web Application Firewall).- security-group:
gather.tf: Terraform script to gather information about security groups.main.tf: Main Terraform configuration for security groups.variable.tf: Definition of variables used in the security group module.
This modular approach enhances the project’s maintainability, making it easier to manage and scale as your infrastructure requirements evolve. Each module focuses on a specific aspect of the infrastructure, promoting reusability and clarity in configuration.
Pre-requisites
Before diving into the infrastructure creation, make sure you have the following:
- An AWS Account
- Terraform installed on your local machine
- AWS Access and Secret Access keys configured
- Domain Name Configured manually and add the Name Servers to your Domain Provider
Step-by-Step Guide
To get started, clone the repository using the following command:
git clone https://github.com/NotHarshhaa/DevOps-ProjectsNavigate to the project folder:
cd DevOps-Projects/DevOps Project-11Planning and Deployment
Execute the following Terraform commands to plan and deploy the infrastructure:
terraform plan -var-file=variables.tfvarsterraform apply -var-file=variables.tfvars --auto-approveOnce the deployment is complete, you can inspect the created services using the provided snippets for each service.
VPC & Other Networking related Services
VPC
Public and Private Subnets
Public and Private Route tables
Internet Gateway
Elastic IP addresses
NAT Gateways
Security Groups
EC2 & AutoScaling Group
Launch template
AutoScaling Group
Target Group & Load Balancer
Target Group
Load balancer
Database
Subnet Group for RDS
RDS Cluster
After Core Service, Deploy Service on Server
Route53
AWS Certificate Manager
AWS Web Application Firewall
CloudFront
IAM Role
IAM Policy
IAM instance profile
TF State file and State lock
Backend- TF State file stored on S3
TF State lock file
Once the deployment is completed, you can enter your domain name in the browser to validate whether your servers are perfectly running or not.
As you can see in the below snippet, the Application is running
Clean-up
When you’re done exploring the Two-Tier architecture and want to avoid incurring unnecessary costs, follow these steps to clean up the resources:
Run the following command to initiate the destruction of the infrastructure.
terraform destroy -var-file=variables.tfvars --auto-approve
Delete the Repository (Optional):
- If you cloned the Git repository for this project and no longer need it, you can delete it locally.
rm -rf DevOps-ProjectsThis step is optional and depends on whether you plan to reuse the repository for future exploration.
By following these clean-up steps, you ensure that AWS resources are properly decommissioned, and you won’t incur unnecessary charges. Always exercise caution when performing destructive actions like terraform destroy to avoid unintended consequences.
Conclusion
In this comprehensive guide, we embarked on a journey to deploy a Two-Tier architecture on AWS using Terraform. Embracing a modular approach with enhanced security measures, our infrastructure is organized into dedicated modules, offering scalability, maintainability, and robust security.
Happy coding!
Feel free to reach out to me if you have any doubts or queries.
LinkedIn- https://www.linkedin.com/in/harshhaa-vardhan-reddy/
GitHub- https://github.com/NotHarshhaa/
Happy Learning!
Harshhaa Vardhan Reddy - DevOps Engineer / Blogger